Managing IAM roles and permissions in BigQuery is essential for maintaining data security and governance. It ensures that non-technical users access only the necessary data, simplifying daily tasks for data analysts while keeping operations secure.
.avif)
For data security analysts, project managers, system administrators, and compliance officers, correctly assigning roles prevents unauthorized access and ensures compliance with governance regulations. This approach helps safeguard data integrity, streamlines workflows, and enhances collaboration across teams working within BigQuery projects.
In BigQuery, IAM roles and permissions are essential for controlling access to datasets and resources by specifying what actions users can perform. Predefined roles, such as BigQuery Data Viewer and Data Editor, handle common tasks, while custom roles provide more tailored access based on specific needs.
By assigning roles at different levels - organization, project, dataset, or table – you ensure secure and appropriate access. This follows the principle of least privilege, allowing users only the permissions required to perform their tasks while safeguarding sensitive data.
BigQuery provides three types of IAM roles for managing access: Predefined roles for common tasks, Custom roles for tailored permissions, and Basic roles like Owner, Editor, and Viewer. These roles help data analysts, security analysts, and project managers ensure secure, efficient access management across BigQuery projects.
Custom roles in BigQuery allow organizations to create tailored access controls by bundling specific permissions. Unlike predefined roles, custom roles provide more granular control, making them ideal for data analysts, security analysts, and project managers who need to enforce precise access levels.
These roles ensure that users only have the permissions necessary to perform their tasks, following the principle of least privilege.
Custom roles must be created within a project or organization and are limited to that scope. Regular maintenance is required, as custom roles do not automatically update with new features or permissions provided by Google.
Predefined roles in BigQuery provide granular access to specific resources, making them ideal for data analysts, security analysts, and project managers responsible for tasks like data discovery and reporting.
Google creates and manages these roles, ensuring they stay up to date with new features and services. This automatic updating allows users to complete their tasks efficiently without needing to manually adjust permissions.
Roles like BigQuery Data Viewer or Data Editor can be assigned at various levels, including organization, project, or resource. This flexibility helps system administrators and compliance officers manage access controls effectively, ensuring data security and compliance across BigQuery environments.
Access to Google BigQuery resources can be granted to a user, group, or service account by assigning one or more roles. These resources can be accessed at different levels, including:
Google Cloud allows users to manage access to BigQuery resources by assigning roles at the organization and project levels. When roles are assigned at the organization level, users gain permission to access all BigQuery resources across the entire organization. This centralized control is useful for large enterprises where multiple teams need access to shared data resources.
At the project level, roles can grant users permission to run BigQuery jobs, access datasets, and perform administrative tasks specific to that project. This enables project managers and system administrators to efficiently manage permissions while ensuring secure and proper access to data within individual projects.
Roles assigned at the dataset level allow users to access specific datasets without full project access. This granular control ensures that users, such as data analysts or business users, only have the necessary permissions, enhancing security and precision in managing access within BigQuery.
Roles can be assigned to individual resources within a dataset, such as tables and views, providing users with access to specific data without full dataset permissions. This approach offers more control, allowing users to work with the necessary data while maintaining security over other resources.
Managing Data Mart access in BigQuery requires understanding two distinct methods: Direct Access and Indirect Access. Each provides unique ways to control data access while ensuring secure and efficient workflows for end users and data analysts.
Direct access allows users to work with Data Marts directly through their own Google Cloud Platform (GCP) credentials. This method ensures full visibility and control over the Data Mart's SQL editor and other related features. Users with direct access can:
This approach is ideal for advanced users, such as data analysts and system administrators, who require complete access to manage and adapt Data Marts to dynamic business needs.
Indirect access introduces a more controlled way to share Data Mart resources without granting full GCP permissions. In this approach, a Data Analyst manages access on behalf of end users.
Here's how it works:
Indirect access is ideal for non-technical users who need to work with reports without managing the technical complexities of SQL or GCP access. This method ensures security, simplifies workflows, and enables effective collaboration between technical and non-technical stakeholders.
Access in BigQuery is managed through IAM policies, which bind users or service accounts to roles on specific resources and their descendants. You can manage access to projects, folders, and organizations using the Google Cloud Console, CLI, REST API, or Resource Manager libraries.
To view current access in BigQuery IAM, use the Cloud Console, gcloud CLI, REST API, or Resource Manager libraries. Navigate to the Google BigQuery IAM page in the Cloud Console, select a project, folder, or organization, and review the list of principals assigned roles. This list also includes principals who inherited roles from parent resources.
To quickly grant or revoke a single role for a principal, you can use the Cloud Console or gcloud CLI without editing the IAM policy directly.
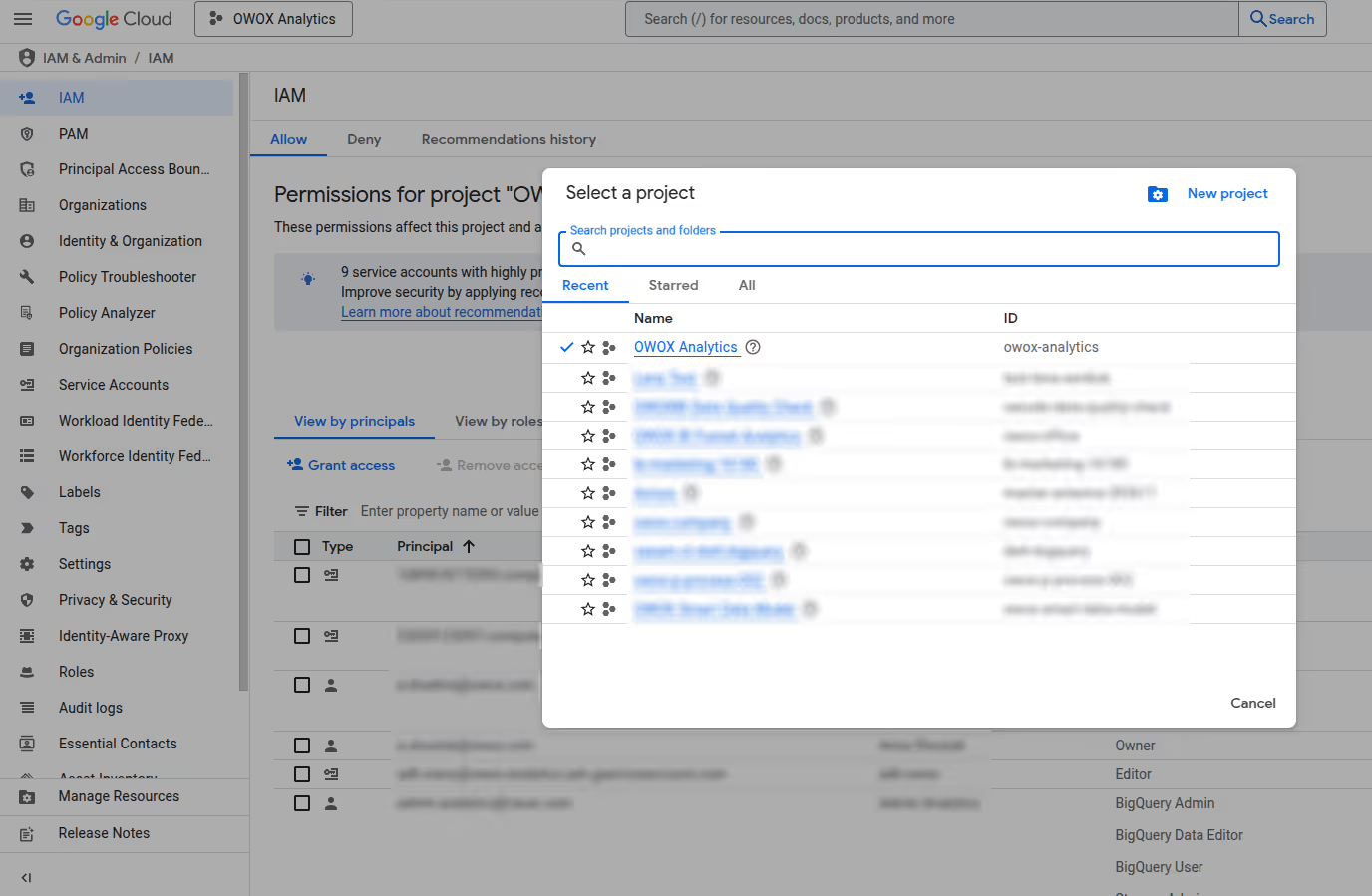


To assign roles across multiple projects, folders, or organizations:
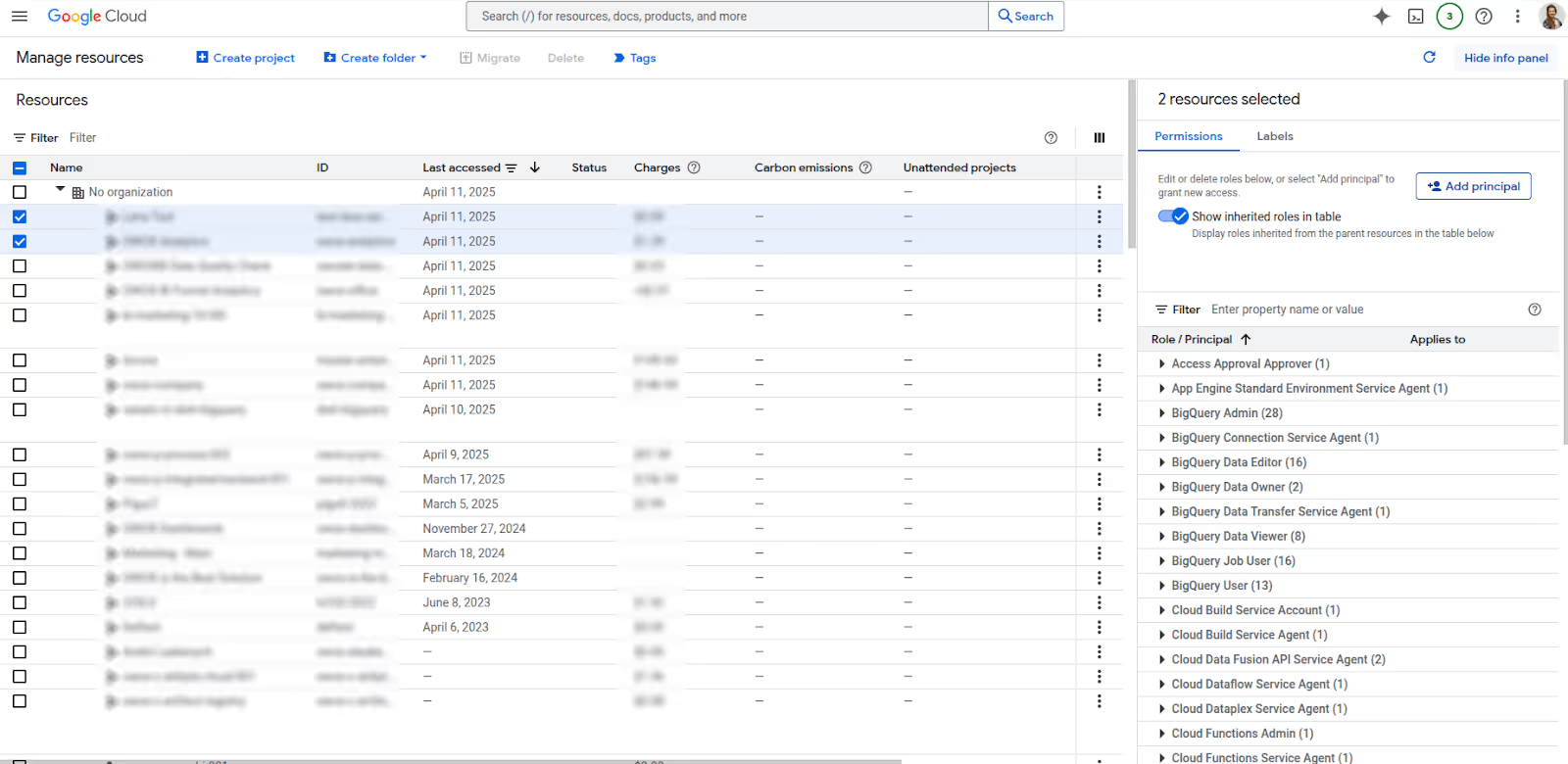

For broader changes, use the read-modify-write approach. First, get the current policy with getIamPolicy(), modify the roles or principals, and apply changes using setIamPolicy() via gcloud CLI, REST API, or client libraries.
Dataset permissions define which users, groups, and service accounts can access its tables, views, and data. While access controls can't be applied during dataset creation in the Cloud Console or bq CLI, they can be applied via the datasets.insert API.
After creation, you can control access using the Cloud Console, GRANT and REVOKE statements, the bq update command, datasets.patch API, or client libraries.
Follow these steps to grant access to a dataset:
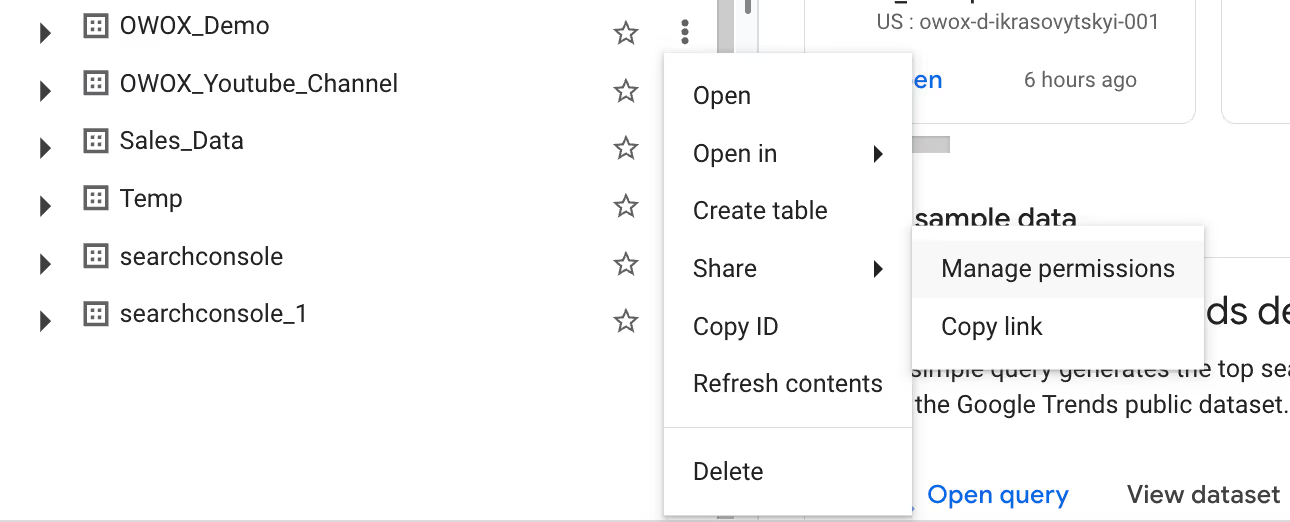

To revoke access to a dataset, follow these steps:



Setting up IAM roles and permissions in BigQuery can be tricky, often resulting in mistakes like granting too much access or misconfiguring permissions. Avoiding these common issues is important to keeping your data secure and allowing teams to work efficiently.
Negative conditions, such as using resource.name != resource, can unintentionally grant overly permissive access by excluding specific resources rather than precisely defining what should be accessible.
This misconfiguration can result in broader access than intended, posing security risks and potentially allowing unauthorized users to access sensitive BigQuery resources.
With IAM Conditions, you cannot add authorized view, authorized routine, or authorized dataset grants. These features require unconditional access, meaning that permissions for these resources must be granted without conditions.
Attempting to apply IAM Conditions will result in failure, limiting the flexibility to control access to these specific resources.
When a user is granted conditional access to a dataset or table, they are unable to modify permissions for that resource using the Google Cloud Console.
Instead, permission changes must be made through the bq command-line tool or API, as the Cloud Console doesn't support modifications for conditionally granted access.
IAM Conditions do not directly support row-level and column-level access control. However, a user with conditional access can potentially assign themselves the BigQuery Admin role (roles/bigquery.admin) on the table.
With this elevated role, they can modify row and column access policies, thereby indirectly controlling data access at a granular level.
Users with conditional access may face limitations when trying to query INFORMATION_SCHEMA views, as these views require broader access permissions.
Since conditional access restricts certain actions based on specific conditions, it can prevent users from accessing the metadata in INFORMATION_SCHEMA, hindering their ability to retrieve important information about datasets, tables, and permissions.
Negative conditions can cause issues when users run queries with wildcards. For example, a condition like resource.name != /projects/my_project/datasets/my_dataset/tables/secret restricts access to the "secret" table.
However, users can bypass this restriction by using a wildcard query like SELECT * FROM my_project.my_dataset.secre*, unintentionally granting access.
Certain BigQuery features, like BI Engine and materialized views, aren't optimized when using tables with row-level access policies. Additionally, row-level security doesn't support query pruning in partitioned tables, though this doesn't affect the main query execution. However, you may notice a slight performance decrease when querying such tables.
Here are key practices for managing IAM roles and permissions in BigQuery to ensure data security and compliance. These strategies help maintain control over access to critical resources, prevent potential data breaches, and streamline user access, ensuring that only the necessary roles are assigned for efficient and secure operations.
Regularly auditing IAM roles is essential to maintaining secure access. By frequently reviewing who has what permissions, project managers and system administrators can ensure that roles are up-to-date and still require users to perform their tasks.
Auditing helps identify misconfigured roles, excessive permissions, or outdated access, enabling timely adjustments and preventing unauthorized access to sensitive BigQuery resources.
Applying the principle of least privilege ensures users are only granted the minimum level of access necessary to perform their jobs. Limiting user permissions to only what is essential reduces the risk of unauthorized actions, data breaches, or accidental errors.
Implementing this principle helps maintain strict security controls and ensures compliance with internal and external data governance policies.
Over time, users may accumulate roles or permissions they no longer need. Regularly cleaning up these unused permissions helps minimize security risks by ensuring that users do not retain unnecessary access to BigQuery resources.
Removing unused roles also simplifies role management, reduces potential access misuse, and keeps access permissions streamlined and secure.
The OWOX Reports for Google Sheets lets you connect your BigQuery data directly to your spreadsheets, giving you real-time insights with minimal effort. This tool simplifies importing data, so both data analysts and business users can build dynamic reports, automate data updates, and visualize key metrics right in Google Sheets.
With customizable reporting features, users can easily filter data, tailor their views, and create charts for clearer analysis. By keeping everything within Google Sheets, teams can work efficiently with large datasets, making it a practical solution for generating insights and helping business decisions.

IAM roles and permissions in BigQuery define what actions users, groups, or service accounts can perform on resources like datasets and tables. These permissions ensure that users can only access the data they are authorized to use, helping maintain security and control over data within a Google Cloud project.

BigQuery offers three main types of IAM roles: predefined roles, custom roles, and basic roles. Predefined roles, like BigQuery Data Viewer and Editor, provide common permissions. Custom roles allow organizations to define specific permissions based on their needs, while basic roles (Owner, Editor, Viewer) offer broader access controls.

Permissions in BigQuery can be managed at various levels: project, dataset, and table/view. Roles assigned at the project level provide broader access, while dataset- and table-level roles offer more granular control. Administrators can manage permissions using the Cloud Console, gcloud CLI, REST API, or IAM policies for flexible control.

Common pitfalls in BigQuery IAM roles include over-permissioning users, neglecting to use the principle of least privilege, and misconfiguring conditional access. Negative conditions, wildcard queries, and row-level security limitations can also cause unintended access issues, potentially exposing sensitive data or leading to performance bottlenecks.

To grant or revoke access to a BigQuery dataset, navigate to the "Share dataset" option in the Cloud Console, choose the dataset, and manage the permissions of specific users or service accounts. You can assign roles such as Viewer, Editor, or Owner, or revoke access by removing assigned roles.

Best practices for managing IAM roles in BigQuery include conducting regular audits of user permissions, following the principle of least privilege by assigning only necessary roles, and cleaning up unused or outdated permissions. This ensures data security, minimizes risks, and maintains efficient control over access to resources.