Content
- What Is Data Processing?
- How Often Should Data Processing Occur in E-commerce?
- What Data Holds Significance in E-commerce?
- Benefits Of Data Processing For An Ecommerce Business
- Are You Collecting the Right Data?
- Is Your Collected Data Merged?
- Can You Process the Data You Collect?
- Is Your Data Secure?
- How Can You Accomplish All This?
- Effective Approaches to E-commerce Data Management
- Challenges in E-commerce Data Management
- Choosing the Best Data Processing Solutions for Your E-commerce Project
- Leveraging Google BigQuery for E-commerce Data Excellence
Who Is in Control of Your Data Processing in E-commerce?
Vlad Flaks, CEO @ OWOX
Get in-depth insights

Get in-depth insights
Ultimate Data Quality Checklist
This article dives into the crucial tasks of e-commerce data processing and provides criteria for assessing data quality in e-commerce projects.
In recent years, the volume of digitized customer behavior data has surged. Traditionally, retailers collected order and customer data in CRM systems and loyalty programs. However, the Internet now provides data from earlier stages of the sales funnel, revealing how customers discover and choose products.

Effective data integration is essential for unifying diverse systems, databases, and applications to ensure seamless integration and comprehensive analysis.
Analyzing this data helps businesses better understand their customers, identify bottlenecks in the sales funnel, and make informed strategic decisions across the organization.
However, the sheer abundance of data often creates the illusion that the business fully owns it. So, what does it truly mean to own your data?
Note: This post was originally published in June 2015 and was completely updated in September 2024 for accuracy and comprehensiveness on marketing analytics.
What Is Data Processing?
Data processing refers to the collection, manipulation, and transformation of data to extract meaningful information or insights. This process involves various steps, such as data cleaning, validation, analysis, and aggregation.
Through data processing, raw data is converted into a more understandable or usable format, enabling decision-makers to identify trends, make predictions, and inform strategic decisions. It plays a crucial role in research, business intelligence, and operational efficiency, leveraging both manual and automated techniques to process data. Effective data visualization can enhance data analysis by providing clearer insights, thereby supporting businesses in overcoming data inconsistencies.
This process enables e-commerce businesses to gain insights into customer preferences, optimize their marketing strategies, manage supply chains efficiently, and enhance the overall shopping experience.
By processing data from website analytics, customer feedback, and sales transactions, e-commerce companies can identify best-selling products, forecast demand, personalize marketing efforts, and improve product recommendations, ultimately driving sales and customer satisfaction.
How Often Should Data Processing Occur in E-commerce?
In e-commerce, the frequency of data processing varies based on the type of data and the specific Key Performance Indicators (KPIs) being monitored.
In e-commerce, the frequency of data processing depends on the type of data and the Key Performance Indicators (KPIs) being monitored:
- Weekly: Essential for monitoring website traffic, social media engagement, and impressions, ensuring a strong online presence.
- Bi-weekly: Ideal for evaluating metrics like Average Order Value (AOV), Cost Per Action (CPA), and shopping cart abandonment rates.
- Monthly: Recommended for analyzing multichannel engagement, reach, and detailed customer interaction metrics.
- Quarterly: Crucial for assessing strategic KPIs such as email click-through rates, Customer Lifetime Value (CLV), and subscription rates.
Streamline Your Marketing Data in One Place
Connect, manage, and visualize all your marketing data easily with OWOX BI. Say goodbye to manual reports and hello to instant insights
4.9
What Data Holds Significance in E-commerce?
E-commerce thrives on data, but knowing which e-commerce data to focus on can give businesses a competitive edge. Data silos can hinder workflow efficiency and create discrepancies in customer experiences if data is not seamlessly integrated and updated.
Here’s a breakdown of the most relevant data for e-commerce:
Impressions
Impressions measure how often your ads or content are seen. This could be through paid ads, search results, or social media. They're crucial because they're directly linked to your budget and marketing efforts.
Reach
Reach indicates the total number of people who have seen your content. This includes email subscribers and social media followers. Increasing your reach through consistent campaigns can significantly boost your brand's visibility.
Engagement
Engagement tracks how people interact with your content, like through clicks, likes, or shares. High engagement means your audience is actively interested in what you're offering.
Cost per Action (CPA)
CPA helps you understand the cost involved in achieving a specific action, like a purchase. It's vital for budgeting and ensuring your marketing efforts are cost-effective.
Social Media Metrics
Engagement metrics such as likes, shares, and comments serve as pivotal benchmarks for evaluating your brand's performance across social media platforms. They reflect your social media engagement's effectiveness.
Shopping Cart Abandonment Rate
This rate shows how many visitors add items to their cart but leave without purchasing. It's essential for identifying issues in the buying process.
Average Order Value (AOV)
AOV is the average amount spent per transaction. It's a critical measure of marketing effectiveness and can be increased through strategies like upselling.
Conversion Rate
The conversion rate is the percentage of visitors who make a purchase. It's crucial to understand the effectiveness of your site and marketing strategies in driving sales.
Customer Retention Rate
This rate measures how well you keep customers over time. High retention rates indicate good customer satisfaction and loyalty.
Customer Lifetime Value (CLV)
Customer Lifetime Value (CLV) signifies the cumulative revenue anticipated from a single customer throughout their relationship with a business. It's a key metric for understanding customer value and brand loyalty.
Churn Rate
The churn rate measures how many customers you lose over a specific period. It's important for assessing customer satisfaction and retention strategies.
Focusing on these data points can help e-commerce businesses tailor their strategies, improve customer engagement, and ultimately drive sales and growth.
Benefits Of Data Processing For An Ecommerce Business
- Enhanced Customer Insights: Data processing helps in analyzing customer behavior, preferences, and buying patterns, enabling personalized marketing and product recommendations.
- Improved Inventory Management: By processing sales and inventory data, businesses can optimize their stock levels, reducing overstock and stockouts.
- Efficient Order Processing: Automated data processing systems streamline order management, from processing to delivery, enhancing customer satisfaction.
- Data-driven Decision-making: Accessing processed and precise data empowers businesses to make well-informed decisions regarding marketing strategies, product development, and pricing.
- Increased Sales and Revenue: By leveraging targeted marketing campaigns and tailored customer experiences derived from analyzed data, businesses can substantially enhance their sales and revenue.
- Market Trend Analysis: Data processing enables businesses to identify and act on emerging market trends, staying ahead of the competition.
- Cost Reduction: Automating data processing tasks enables businesses to cut operational costs linked with manual data entry and analysis.
- Risk Management: Analyzed data can uncover potential risks and challenges, enabling businesses to formulate strategies for their mitigation.
- Enhanced Customer Service: Analyzing customer feedback and support data helps businesses improve their service, addressing common issues and concerns.
- Scalability: Data processing systems can grow with the business, handling increasing volumes of data efficiently and without significant additional costs.
- Collaboration on Data-related Projects: Emphasizing collaboration and data sharing in data-related projects enhances teamwork and ensures seamless progress, with features like version control playing a crucial role.
These benefits highlight the critical role of data processing in the growth and success of e-commerce businesses, enabling them to operate more efficiently, understand their customers better, and make strategic decisions based on insights derived from their data.

Gain clarity for better decisions without chaos
No switching between platforms. Get the reports you need to focus on campaign optimization
Are You Collecting the Right Data?
To start with, information about user activity must be recorded and stored in a database available to you, free from «noise» that can reduce the value of the data. You are most likely confident that this is working properly in your business, but here are the first two questions that you need to be able to answer:
- Do you record each block and product impression for each customer?
- Do you filter your employee visits out from user visits?
If your customers give you signals, but you do not save them – you are not in control of your data.
Is Your Collected Data Merged?
Services and software are abundant, that record user actions, scattering the data out:
- Online campaign data is stored in various advertising services.
- Users’ onsite or mobile app activity is collected in an online analytics system.
- Real sales data, including margins, order completion rates, and adjustments, are processed in an ERP or CMS.
To assess the impact of your efforts on the results, the cost of customer acquisition, and the income from these customers, you should be able to merge and correlate the data from all these systems through effective data integration.
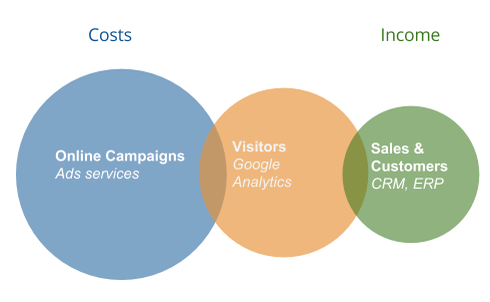
If you can not collect all your data in one system, you are not in control of your data.
Can You Process the Data You Collect?
Now that you have collected terabytes of your beloved data, there is just one thing left to do: process it. Most likely, it is too much for Excel or a standard database to handle, so you will need specialized software that can crunch vast amounts of e-commerce data.
Fortunately, the market has several customized solutions to choose from, but do they let you keep control over your data? The two questions you need to ask are:
- Can you process the data in just a few seconds, regardless of size?
- Can you perform ad-hoc queries to the data, not just pre-defined reports?
If you need to wait several hours for your reports during your peak sales season, and the structure of the reports is pre-defined, your data is useless. You don’t control your data, and your data controls you.
Is Your Data Secure?
Processing large amounts of data requires hardware as well as software. Hard drives fail and information can be lost. If you are not confident about the safety of your data – you are not in control of your data. Okay, you own it, but temporarily. It’s only a matter of time until you lose it. Protecting sensitive customer data through robust data encryption and security measures is crucial to maintaining trust and ensuring data integrity.
What does it mean for a business to really be in control of its data?
It means that they collect all the necessary information, can merge and correlate it quickly, can process it regardless of size, and are sure that they won’t lose it.
How Can You Accomplish All This?
There are several different ways to take control of your data. I want to give you four main reasons why we use Google BigQuery to do this.
1. Applications like it
Most requests for data processing are made by programs, not people. There is a great set of SDKs for various programming languages, support for ODBC drivers, and the ability to work with Google BigQuery from the command line.
2. IT departments love it
This shouldn’t be surprising because there is no need to maintain servers, provide parallelized computing, create indexes, and deal with backups.
3. Management loves it
Google BigQuery can process any amount of data in just a few seconds, and your IT department will never ask for more servers. You also don’t need to buy expensive licenses or enter into long-term contracts.
4. The future loves it
In today’s digital world, you never know exactly what questions you will need to answer in the future or what services you will need. However, with Google BigQuery, you can be confident that your data will stay under your control and that you will always be able to process it or transfer it to an external service.
Dive deeper with this read
Google BigQuery: The Best Marketing Data Warehouse

Effective Approaches to E-commerce Data Management
E-commerce data management is crucial for the growth and efficiency of online businesses.
Here are the best practices for e-commerce data management:
A product data management system is a comprehensive solution for handling essential product information, including inventory data, specifications, pricing, and supplier details.
It plays a vital role in syncing and organizing data across sales channels, enabling better collaboration among stakeholders and improving inventory management for evaluating market trends.
Determine Business Objectives and Goals
Identify what data is essential for your business objectives. Not all data points are equally valuable, so focus on those that align with your goals, such as increasing conversions or improving customer satisfaction.
Establish a Data Governance System
Deploy stringent security measures to safeguard sensitive data. This includes data encryption, firewalls, SSL certificates, and two-factor authentication. Regularly update and review your security policies to comply with industry standards.
Use Data Management Tools
Leverage both Product Data Management (PDM) and Customer Data Management (CDM) systems. These tools automate data intake, organize data efficiently, and help secure and cleanse your data for better decision-making.
Appoint Data Stewards
Designate a team of experts responsible for managing your data, setting security protocols, and granting data access permissions. This can be managed internally or outsourced to specialized firms.
Challenges in E-commerce Data Management
Managing data in e-commerce poses intricate challenges due to the vast volume, variety, and velocity of information, necessitating robust strategies for efficient storage, retrieval, and analysis. Online transactions, including online shopping and electronic payments, have grown in popularity, making it crucial to manage the data generated through these interactions to facilitate insights and improve business strategies. Here are a few challenges:
Online and In-store Data Synchronization
Maintain coherence between online and In-store outlets through the adoption of a Product Data Management (PDM) system, facilitating seamless integration of product information and delivering a cohesive brand experience across all channels.
Supply Chain Disruptions
Manage data from external partners accurately to keep the fulfillment team informed and provide customers with precise delivery information.
Customer Data Security and Privacy
Safeguard customer data through the utilization of secure and encrypted Customer Data Management (CDM) systems. Utilize machine learning algorithms to identify and thwart fraudulent activities and potential data breaches.
By adhering to these recommended strategies, e-commerce enterprises can efficiently oversee their data, resulting in better decision-making, elevated customer satisfaction, and, ultimately, business expansion.
Streamline Your Marketing Data in One Place
Connect, manage, and visualize all your marketing data easily with OWOX BI. Say goodbye to manual reports and hello to instant insights
4.9
Choosing the Best Data Processing Solutions for Your E-commerce Project
Choosing the right data processing solutions is crucial for the success of your e-commerce project. Here are key points to consider when selecting the best data processing solutions:
- Scalability: Opt for solutions that can scale with your business growth, handling increased data volumes without performance degradation.
- Real-time Processing: Choose solutions capable of processing data in real time, enabling immediate insights into customer behavior and operational efficiency.
- Integration Capabilities: Ensure the solution integrates seamlessly with your existing e-commerce platform, CRM, ERP, and other tools to create a cohesive data ecosystem.
- Data Security: Give precedence to solutions equipped with strong security functionalities to safeguard sensitive customer and business data, incorporating encryption, access controls, and adherence to data protection regulations.
- Cost-Effectiveness: Consider the total cost of ownership, including setup, maintenance, and scaling costs. Look for solutions that offer a good balance between features and price.
- User-Friendly Interface: Select solutions with intuitive interfaces and dashboards, making it easier for your team to analyze data and derive actionable insights.
- Customization and Flexibility: The solution should be customizable to fit your specific e-commerce needs and flexible enough to adapt to changing business requirements.
- Support for Multiple Data Sources: Choose solutions that can handle data from various sources, including website traffic, social media, customer feedback, and transaction records.
- Advanced Analytics and Reporting: Opt for solutions that offer advanced Data Analytics for e-commerce features, including predictive analytics, customer segmentation, and personalized reporting capabilities.
- Vendor Reputation and Support: Research the solution provider’s reputation, customer support services, and the responsiveness of their technical support team.
- Compliance and Data Governance: Ensure the solution complies with relevant data protection laws (e.g., GDPR, CCPA) and supports data governance best practices.
- Machine Learning and AI Capabilities: Consider solutions that incorporate machine learning and AI for advanced e-commerce data analysis, trend prediction, and automation of routine tasks.
- Community and Ecosystem: Look into the solution’s community and ecosystem for additional plugins, integrations, and resources to enhance its functionality.
By carefully evaluating these points, you can select a data processing solution that not only meets your current e-commerce needs but also supports future growth and innovation. Effective e-commerce data management involves best practices, addressing challenges, and utilizing various systems to optimize operations, predict trends, and secure sensitive customer information.
Leveraging Google BigQuery for E-commerce Data Excellence
Google BigQuery stands out as an indispensable tool for e-commerce data management, offering a blend of scalability, speed, and cost-effectiveness that is hard to match. With its sturdy infrastructure and effortless integration capabilities, this platform establishes a reliable base for e-commerce operations to handle extensive data volumes efficiently.
This enables swift adaptation to market fluctuations and customer preferences. The ability to perform real-time Data Analytics for e-commerce and leverage advanced machine learning within the same platform further empowers e-commerce businesses to stay ahead of the curve, making predictive decisions that enhance customer experiences and drive sales.
Moreover, BigQuery's serverless architecture and strong security features alleviate the burdens of infrastructure management and data protection, allowing businesses to focus more on strategic growth initiatives rather than operational challenges.
The flexibility to access data from anywhere and the ease of sharing insights across teams foster a collaborative environment that is crucial for the fast-paced e-commerce industry. By harnessing the power of Google BigQuery, e-commerce businesses can unlock new opportunities for innovation and efficiency, positioning themselves for success in a competitive digital marketplace.
Spend Smarter, See Results Sooner
Learn how to optimize every marketing dollar with personalized insights from OWOX BI
FAQ
-
What is data processing in e-commerce?
Data processing in e-commerce involves collecting, organizing, and analyzing data from online transactions, customer interactions, and market trends to make informed business decisions. It enables e-commerce platforms to optimize operations, personalize customer experiences, and improve product offerings.
-
How data is used in e-commerce?
Ecommerce data is used to understand customer behavior, forecast demand, optimize inventory, tailor marketing strategies, and enhance user experiences. Analyzing sales data, customer feedback and website analytics helps businesses increase conversions, retain customers, and drive growth.
-
How do I manage data on my e-commerce website?
Managing data on an e-commerce website involves implementing robust data collection and storage systems, ensuring data security and privacy, and regularly analyzing data for insights. Utilizing e-commerce platforms with built-in analytics, employing data management tools, and adhering to data protection regulations are key to effective data management.
-
Who is in control of your data when you use a website or app?
- When you use a website or app, the entity that owns and operates that platform typically has control over your data. They can collect, process, and store your personal information as outlined in their privacy policy. However, it's important to note that data protection regulations like the GDPR give users certain rights and protections regarding their personal data. -
What rights do you have regarding your personal data?
- As a user, you have various rights regarding your personal data. These can include the right to access, correct, or delete your data, as well as the right to restrict or object to its processing. You also have the right to know how your data is being used and if it's being shared with any third parties. These rights are typically outlined in the privacy policy of the website or app you are using. -
How can you protect your data when using websites or apps?
- There are several steps you can take to protect your data when using websites or apps. Firstly, ensure you only provide necessary personal information and avoid sharing sensitive details unless absolutely necessary. Be cautious when granting permissions to access your data and review privacy settings. Regularly update your passwords and use strong, unique ones for each platform. Additionally, consider using antivirus or anti-malware software and be skeptical of suspicious emails or links that may lead to phishing attempts.
Get in-depth insights

Get in-depth insights
Ultimate Data Quality Checklist



